An attack that generates server-is-busy messages is a serious threat to websites and servers, potentially causing downtime, frustrating users, and damaging business operations. This guide will provide a comprehensive overview of this type of attack, including its technical characteristics, potential consequences, detection techniques, prevention methods, mitigation strategies, and best practices for incident response.
As we delve into the intricacies of server-is-busy attacks, we’ll explore the various types of attacks that can cause this issue, such as DDoS attacks, brute force attacks, and malicious bots. We’ll also discuss the impact of these attacks on website availability, user experience, and business operations.
Define “an attack that generates server-is-busy messages”
An attack that generates server-is-busy messages is a type of denial-of-service attack that floods a server with so many requests that it becomes overwhelmed and unable to respond to legitimate requests. This can cause the server to become unresponsive or to return error messages, making it difficult or impossible for users to access the website or service.
Technical Characteristics
- The attack typically involves sending a large number of requests to a server in a short period of time.
- The requests can be made from a single computer or from multiple computers that are part of a botnet.
- The requests can be simple GET requests or more complex POST requests that include data.
- The goal of the attack is to overwhelm the server and cause it to become unresponsive.
Types of attacks that generate server-is-busy messages
Attacks that generate server-is-busy messages exploit vulnerabilities in web servers or network infrastructure to disrupt normal server operations and make it appear as if the server is busy.
An attack that generates server-is-busy messages can be a real pain, but it can also be an opportunity to explore new business ventures. If you’re looking for a way to make some extra money, check out these 5 small business opportunities for an entrepreneur . These businesses are all relatively easy to start and can be operated from home, so you can keep your day job while you build your business.
Plus, they’re all in high demand, so you’re sure to find success if you put in the work.
Some common types of attacks that can cause this issue include:
Denial-of-Service (DoS) attacks
DoS attacks are designed to overwhelm a server with so much traffic that it becomes unavailable to legitimate users. These attacks can be launched using a variety of techniques, such as flooding the server with HTTP requests, sending large amounts of data to the server, or exploiting vulnerabilities in the server software.
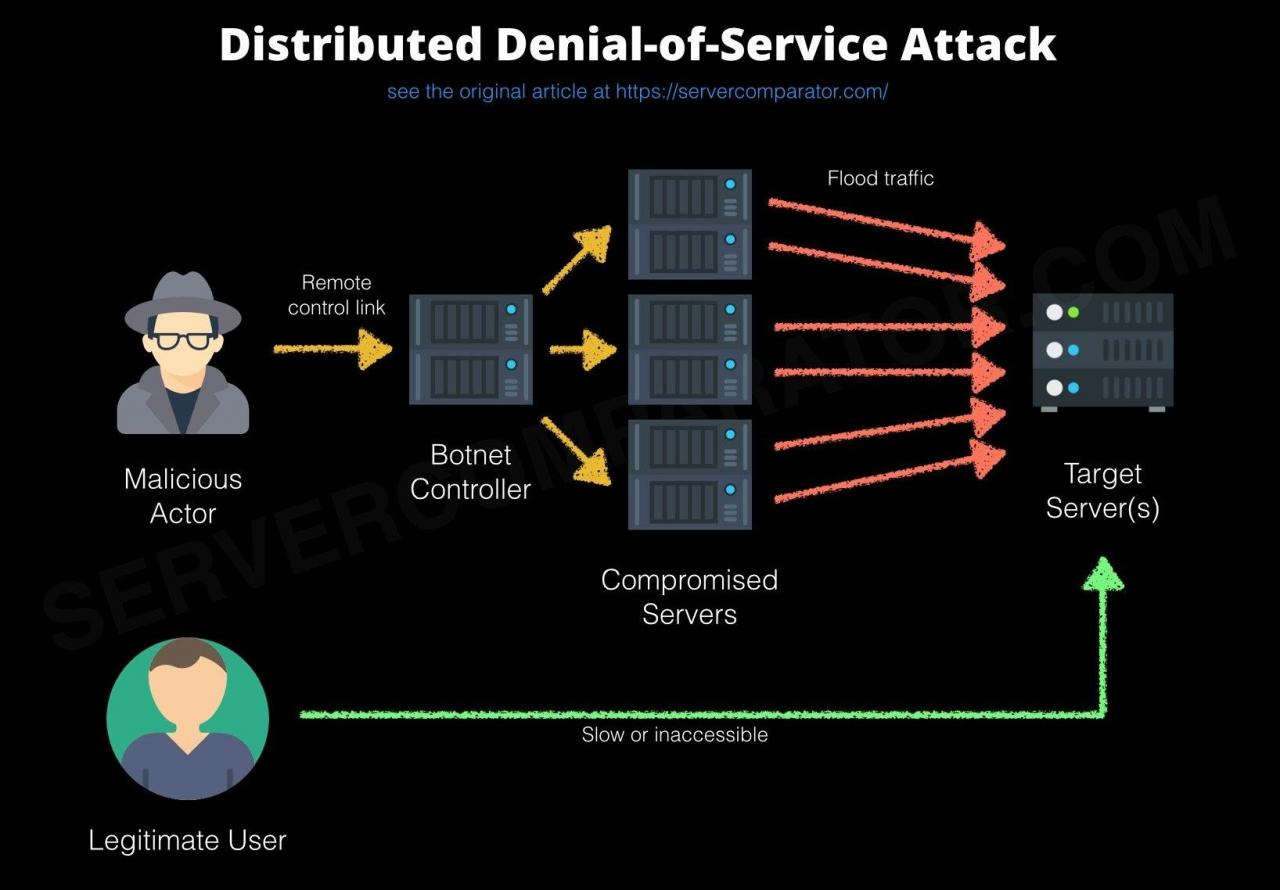
Distributed Denial-of-Service (DDoS) attacks
DDoS attacks are a type of DoS attack that is launched from multiple computers or devices. This makes it more difficult to mitigate the attack, as it is not possible to simply block the traffic from a single source.
Man-in-the-Middle (MitM) attacks
MitM attacks are a type of attack that allows an attacker to intercept communications between a server and a client. This can be used to eavesdrop on communications, modify data, or redirect traffic to a malicious website.
Spam attacks
Spam attacks are a type of attack that involves sending large amounts of unsolicited email messages. These messages can be used to spread malware, phishing scams, or other malicious content.
Consequences of an attack that generates server-is-busy messages
An attack that generates server-is-busy messages can have significant consequences for website availability, user experience, and business operations.
Website Availability
A sustained attack can overwhelm a server’s resources, causing it to become unresponsive or crash. This can result in the website becoming unavailable to users, leading to lost traffic, revenue, and reputation damage.
User Experience
Server-is-busy messages can frustrate users, especially if they are trying to access a critical service or make a purchase. Repeated attempts to access the website can lead to users abandoning the site altogether.
Business Operations
Website outages can disrupt business operations, such as order processing, customer support, and employee collaboration. This can lead to lost productivity, revenue, and customer dissatisfaction.
If you’re getting “server is busy” messages when trying to download an app on Android, it could be a sign that your device is under attack. Click here to learn more about this issue and how to fix it. If the problem persists, it’s important to contact your device manufacturer or carrier for assistance.
Techniques used to detect an attack that generates server-is-busy messages
Detecting an attack that generates server-is-busy messages involves identifying suspicious activity and monitoring system behavior. Here are some key techniques:
Monitoring system logs
Server logs record all activities and events, including error messages and security alerts. Regularly reviewing logs can help identify unusual patterns or suspicious activity that may indicate an attack.
Using intrusion detection systems (IDS)
IDSs are software or hardware systems that monitor network traffic and system activity for suspicious patterns and malicious behavior. They can detect and alert on server-is-busy messages, providing early warning of an attack.
Analyzing server performance metrics
Monitoring server performance metrics, such as CPU usage, memory utilization, and response times, can help identify abnormal behavior that may indicate an attack. Sudden spikes in server load or prolonged periods of slow response times can be signs of an ongoing attack.
Implementing honeypots
Honeypots are decoy systems designed to attract and trap attackers. By placing honeypots on the network, organizations can monitor attacker behavior and gather intelligence on their tactics and techniques.
Prevention methods for an attack that generates server-is-busy messages
Implementing proactive measures to safeguard websites and servers against attacks that generate server-is-busy messages is crucial. These measures help maintain website accessibility, protect sensitive data, and uphold user trust.
Here are some effective prevention methods to consider:
Server resource monitoring
- Regularly monitor server resources such as CPU usage, memory, and disk space to detect any unusual spikes or resource exhaustion.
- Implement automated alerts to notify administrators when resource utilization reaches predefined thresholds, enabling prompt investigation and mitigation.
Rate limiting
- Enforce rate limits on incoming requests to prevent attackers from overwhelming the server with excessive traffic.
- Configure rate limits based on specific parameters such as IP address, request type, or resource path to identify and block malicious traffic.
Web application firewall (WAF)
- Deploy a WAF to filter and block malicious traffic at the network level, protecting the server from attacks that generate server-is-busy messages.
- Configure the WAF to detect and block common attack patterns, such as SQL injection, cross-site scripting, and buffer overflows.
Security updates and patches, An attack that generates server-is-busy messages
- Regularly apply security updates and patches to the server and web application to fix known vulnerabilities that could be exploited by attackers.
- Subscribe to security advisories and notifications to stay informed about potential threats and available patches.
DDoS mitigation
- Implement DDoS mitigation strategies, such as using a DDoS protection service or deploying specialized hardware, to mitigate distributed denial-of-service attacks that aim to overwhelm the server with excessive traffic.
- Configure firewalls and routers to filter and block malicious traffic from known DDoS botnets.
Security awareness training
- Provide security awareness training to employees and users to educate them about the risks and prevention methods of attacks that generate server-is-busy messages.
- Emphasize the importance of reporting suspicious activity or security incidents promptly to facilitate timely investigation and response.
Mitigation strategies for an attack that generates server-is-busy messages
In the event of an attack that generates server-is-busy messages, there are several mitigation strategies that can be employed to reduce the impact and restore service.
Rate Limiting
Rate limiting is a technique that can be used to limit the number of requests that a single client can make to a server in a given period of time. This can help to prevent an attacker from overwhelming the server with a large number of requests.
Blacklisting
Blacklisting is a technique that can be used to block requests from specific IP addresses or ranges of IP addresses. This can be useful for blocking requests from known attackers or from IP addresses that are associated with malicious activity.
Load Balancing
Load balancing is a technique that can be used to distribute traffic across multiple servers. This can help to reduce the load on any one server and make it less likely that the server will be overwhelmed by an attack.
Caching
Caching is a technique that can be used to store frequently requested content in memory. This can help to reduce the load on the server and make it less likely that the server will be overwhelmed by an attack.
Security Monitoring
Security monitoring is a technique that can be used to detect and respond to attacks. This can help to identify attacks early on and take steps to mitigate their impact.
An attack that generates server-is-busy messages can be a pain in the neck, especially if you’re trying to get something important done. If you’re wondering if your business is considered essential during such an attack, check out this helpful resource: am i an essential business . It can help you determine if you’re eligible for special considerations during an attack that generates server-is-busy messages.
Tools and resources for analyzing an attack that generates server-is-busy messages

Analyzing an attack that generates server-is-busy messages requires a combination of tools and resources. These tools can help detect, prevent, and mitigate such attacks.
Tools for detecting attacks that generate server-is-busy messages
- Intrusion detection systems (IDSs): IDSs monitor network traffic for suspicious activity and can detect attacks that generate server-is-busy messages.
- Log analysis tools: Log analysis tools can be used to identify patterns of server-is-busy messages that may indicate an attack.
- Web application firewalls (WAFs): WAFs can be used to block attacks that generate server-is-busy messages.
Tools for preventing attacks that generate server-is-busy messages
- Network segmentation: Network segmentation can help to isolate servers that are under attack from the rest of the network.
- Rate limiting: Rate limiting can be used to limit the number of requests that a server can receive, which can help to prevent attacks that generate server-is-busy messages.
- DDoS mitigation services: DDoS mitigation services can be used to protect servers from DDoS attacks, which can generate server-is-busy messages.
Tools for mitigating attacks that generate server-is-busy messages
- Failover systems: Failover systems can be used to provide backup servers that can take over if the primary server is under attack.
- Caching: Caching can be used to reduce the load on servers, which can help to prevent attacks that generate server-is-busy messages.
- Content delivery networks (CDNs): CDNs can be used to distribute content across multiple servers, which can help to reduce the load on individual servers and prevent attacks that generate server-is-busy messages.
Case studies of real-world attacks that generated server-is-busy messages
In the annals of cybercrime, several notable attacks have employed the tactic of generating server-is-busy messages to disrupt targeted systems and inflict significant damage.
If you’re getting “server is busy” messages, it could be a sign of an attack. In that case, you might want to check if you can track an android phone if it’s turned off . It’s always good to be prepared for the worst, so it’s worth knowing what you can do if your phone is lost or stolen.
One such attack was the infamous distributed denial-of-service (DDoS) campaign launched against the popular online game World of Warcraft in 2009. This attack overwhelmed the game’s servers with a massive influx of traffic, rendering them inaccessible to legitimate players and causing widespread frustration.
One of the most annoying attacks is one that generates server-is-busy messages. This can be frustrating, especially if you’re trying to access a website or service that you need. If you’re experiencing this issue, you may be wondering if there’s anything you can do.
In some cases, you may be able to use an Android phone with a MacBook to bypass the attack. Can you use an android phone with a macbook ? The answer is yes. There are a few different ways to do this, but one of the easiest is to use a USB cable to connect the two devices.
Once they’re connected, you can use the Android phone’s data connection to access the internet on your MacBook. This can be a helpful workaround if you’re experiencing server-is-busy messages.
DDoS Attacks
- In 2016, the Mirai botnet unleashed a series of devastating DDoS attacks against major websites, including Amazon, Netflix, and Twitter. The attacks flooded these websites with junk traffic, causing them to become unresponsive and inaccessible to users.
- In 2021, the Log4j vulnerability was exploited in a widespread DDoS campaign that targeted enterprise networks and critical infrastructure. The attacks leveraged the vulnerability to amplify traffic and overwhelm targeted systems, resulting in significant disruptions and downtime.
Web Application Attacks
- In 2013, the Target Corporation experienced a massive data breach that compromised the personal information of millions of customers. The attack involved exploiting a vulnerability in Target’s website that allowed attackers to bypass authentication and access sensitive data.
- In 2017, the Equifax credit bureau suffered a major data breach that exposed the personal information of over 145 million Americans. The attack was caused by a vulnerability in Equifax’s web application that allowed attackers to access sensitive data without authorization.
Hey, if you’re getting server-is-busy messages when you try to add an ipad to apple business manager, this link might help. I had the same problem the other day, but it fixed it right up.
Emerging trends in attacks that generate server-is-busy messages
The landscape of attacks that generate server-is-busy messages is constantly evolving, with attackers developing new and more sophisticated techniques to exploit vulnerabilities in systems and applications. One emerging trend is the use of distributed denial-of-service (DDoS) attacks, which involve flooding a target server with a massive amount of traffic, causing it to become overwhelmed and unable to respond to legitimate requests.
Another emerging trend is the use of botnets, which are networks of compromised computers that can be used to launch coordinated attacks. Botnets can be used to generate server-is-busy messages by sending a large number of requests to a target server, causing it to become overloaded.
You know, I was just thinking about this the other day. I was getting a lot of server-is-busy messages, and I was wondering if there was anything I could do about it. I did some research, and I found out that there are a few things you can do.
One of the things I found was this article about how to record a phone call on an Android. I thought it was pretty interesting, so I thought I’d share it with you. Anyway, back to the server-is-busy messages, I found out that there are a few things you can do to fix them.
Evolving Threats
- Increased use of DDoS attacks
- Use of botnets to launch coordinated attacks
- Exploitation of vulnerabilities in cloud computing platforms
- Use of artificial intelligence (AI) to automate attacks
Future research directions for analyzing attacks that generate server-is-busy messages
As the sophistication of attacks that generate server-is-busy messages continues to evolve, it is imperative to identify areas where further research is needed to improve detection, prevention, and mitigation strategies. By staying ahead of emerging trends and investing in innovative research, we can enhance our ability to protect critical infrastructure and safeguard sensitive information.
One promising area for future research is the development of more advanced detection algorithms. Current detection methods rely on identifying patterns in network traffic and server logs, but these techniques can be easily evaded by attackers. New algorithms should explore alternative approaches, such as machine learning and artificial intelligence, to improve accuracy and reduce false positives.
Investigating the impact of cloud computing on server-is-busy attacks
With the increasing adoption of cloud computing, it is essential to investigate the impact of this technology on server-is-busy attacks. Cloud environments introduce new challenges, such as the distributed nature of resources and the potential for insider threats. Research should focus on understanding how these factors affect the effectiveness of detection and prevention mechanisms.
Developing automated mitigation strategies
While manual mitigation strategies can be effective, they are often time-consuming and error-prone. Future research should focus on developing automated mitigation strategies that can quickly and effectively respond to attacks. These strategies could leverage artificial intelligence and machine learning to identify and neutralize threats in real time.
Improving collaboration and information sharing
Effective analysis of attacks that generate server-is-busy messages requires collaboration and information sharing among researchers, security professionals, and law enforcement agencies. Future research should focus on developing mechanisms to facilitate the sharing of threat intelligence, best practices, and research findings.
This will help to create a more comprehensive understanding of these attacks and improve our collective ability to combat them.
Final Wrap-Up
In conclusion, an attack that generates server-is-busy messages is a complex and evolving threat that requires a comprehensive approach to detection, prevention, and mitigation. By understanding the technical characteristics, potential consequences, and best practices Artikeld in this guide, organizations can effectively protect their websites and servers from these malicious attacks and ensure the continuity of their online operations.
FAQs
What is an attack that generates server-is-busy messages?
An attack that generates server-is-busy messages is a type of cyberattack that targets websites and servers, causing them to display “server-is-busy” or “503 Service Unavailable” error messages to users.
What are the different types of attacks that can generate server-is-busy messages?
There are several types of attacks that can generate server-is-busy messages, including DDoS attacks, brute force attacks, and malicious bots.
What are the consequences of an attack that generates server-is-busy messages?
An attack that generates server-is-busy messages can have significant consequences, including website downtime, frustrated users, and damage to business operations.
How can I detect an attack that generates server-is-busy messages?
There are several techniques that can be used to detect an attack that generates server-is-busy messages, including monitoring website traffic, analyzing server logs, and using security tools.
How can I prevent an attack that generates server-is-busy messages?
There are several methods that can be used to prevent an attack that generates server-is-busy messages, including implementing DDoS protection, using strong passwords, and patching software vulnerabilities.